Blog
Data Protection for Sharing Data Between High and Low Environments
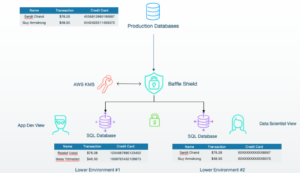
For most IT environments, protecting data as it moves from a high environment (where software or a product is live and customer-facing) to a low…
Privacy-preserving Analytics: The Future of Data Protection Services & Data Security is Now
When Mark Campbell, the chief innovation officer at EVOTEK, asked me to discuss an article he was writing on the quest for mainstream adoption of privacy-preserving…
The Secret to Secure Data? Supporting Your CISO
Few executive positions are as pressure-packed as the chief information security officer (CISO). In one study, 21% of CISOs said their companies offered no support…
Ameesh Divatia appears on theCUBE at AWS re:Inforce to talk about proxy architecture and the future of data security
Baffle CEO Ameesh Divatia talks with John Furrier of theCUBE at the AWS re:Inforce 2022 Security Conference for Amazon Web Services. Since compliance is driving…
AWS s3 Encryption and Data Protection
Having just returned from AWS’s security event, re:Inforce, in Boston, after a three-year hiatus, I was inspired and encouraged by what I learned looking around…
As Compliance Requirements Mount, Companies Struggle to Bring Data Security and Privacy Practices up to Speed
The compliance landscape is becoming more complex for U.S. companies, especially those conducting business in multiple states and internationally. In 2022 alone, Connecticut and Utah…
Cloud Security – Securing Cloud AI Data Pipelines
Recent attacks on Jupyter Notebook show threat actors exploit cloud-based data science platforms. And as companies are transitioning from on-premises data centers to private cloud,…
How to Secure Data in a ‘Need-To-Share’ Business Environment
For decades, data was siloed and locked away, and there were limited reasons for accessing this valuable asset, let alone sharing it. As such, data…
How to De-Identify Your Data in IBM Cloud with Baffle Data Protection Services
IBM Cloud offers an extensive portfolio of cloud-native databases that IBM provides as secure, production ready, and fully managed database technologies, to enable developers to…
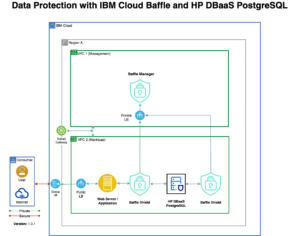
Step by Step Guide for Data Protection with Baffle and IBM Cloud Hyper Protect DBaaS for PostgreSQL
Introduction: IBM Cloud and Baffle Data Protection Services (DPS) for IBM Cloud enable provisioning of Baffle Manager and Baffle Shield and configure database encryption/decryption rules…