Cloud-based databases need new approaches to ensure data security
Interest and adoption of cloud-based databases is ramping up as more companies see the value of moving from traditional on-premise IT infrastructures to off-premise cloud services like Amazon (AWS), Microsoft Azure and many others.
Database-as-a-Service (DBaaS) offers high availability, multi-tenancy and the ability to scale as demand grows without the high cost of buying new hardware and related maintenance costs. The game company Zynga, for example, said a cloud service (in this case, Amazon’s Aurora database) “…has delivered the necessary performance without any of the operational overhead of running MySQL.”
But security with cloud computing is a concern as IT moves away from controlling the physical IT infrastructure to managing data housed by the third-party cloud supplier. Since data, the crown jewels of a business, resides in enterprise databases, it must be protected at all costs.
While cloud services make every effort to secure their systems, they are not infallible. This fact is clearly evident in cloud service providers’ service agreement with their customers where they clearly state that the security of the system and data is a shared responsibility between the customer and the provider. When it comes to protecting the data, the leading cloud providers will recommend that customers build security mechanisms in the application in addition to using security features offered by the cloud provider.
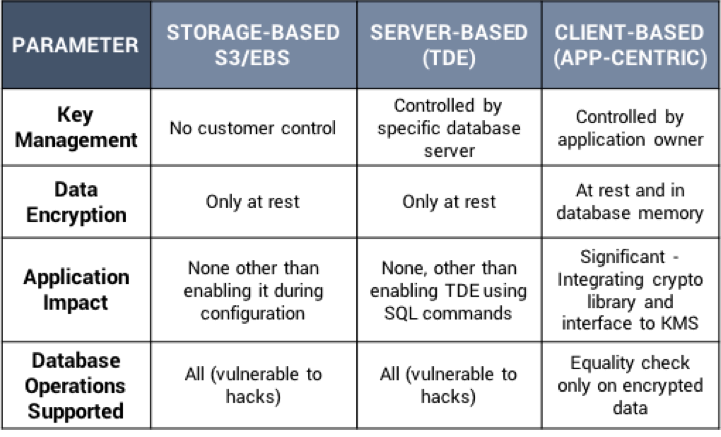
For example, the most basic encryption capability available in the cloud is where the storage containers, Simple Storage Service (S3) object store instances or Elastic Block Store (EBS) storage volumes are automatically encrypted based on user preference during setup.
Database vendors such as Microsoft and Oracle offer database server-based encryption options (also known as Transparent Data Encryption (TDE) as they are transparent to the application) that offer slightly better security. But, in both of these cases, the data can be accessed by the DBaaS provider since it is only encrypted at rest and exposed in the database server.
Application-based encryption addresses this threat by encrypting the data before it is sent to the cloud database. However, such an approach usually requires that application developers learn cryptography and key management best practices, identify the right place in the application architecture to perform encryption, and make the right function calls to encrypt and decrypt sensitive data as it is stored in the database. Furthermore, the only operation that is possible on encrypted data is equality check meaning that nearly all operations previously performed by the database on the data would have to be done after the data is extracted from the database and decrypted in the application. Finally, many companies use third party applications that cannot be modified to incorporate application encryption.
State of database encryption
In the case of cloud services, the provider typically gives you, the customer, some control of the keys used for encryption and decryption. But, be careful what you ask for because now you are solely responsible for generating, maintaining, rotating (as required by compliance regulations) and retiring keys on an ongoing basis. This does not protect against a breach of the cloud service because these keys have to be provided to the cloud in order to perform operations on that data.
Protect data as soon as it’s created
The most comprehensive solution is prevention at the data record level. Protecting the data as soon as it is created using impenetrable encryption algorithms like AES will make the data unusable without the corresponding encryption keys used to encrypt it. The next step is to make sure that the keys are never available in the same domain and separated from the encrypted data. This will ensure that getting access to the data store will not compromise the data as it will only yield encrypted data. Implementing such a scheme requires efficient encryption management capabilities that are not prevalent right now.
As a result, encryption today is grossly underutilized. Breach Level Index reports that out of the 5.9 billion records that have been lost or stolen since 2013, only 4% consisted of encrypted data that was essentially useless to the hacker. But as the awareness of the benefits of encryption grows, we will see solutions that allow for easier adoption along with key management and sophisticated monitoring becoming more prevalent in the enterprise.
DBaaS has a promising future if service providers can assure their customers that their data is safe. Innovative approaches will be necessary to achieve those goals. It’s also important to note these new solutions can’t interfere with existing workflows if they are to be widely adopted.
Join our newsletter
Schedule a Demo with the Baffle team
Meet with Baffle team to ask questions and find out how Baffle can protect your sensitive data.
Easy
No application code modification required
Fast
Deploy in hours not weeks
Comprehensive
One solution for masking, tokenization, and encryption
Secure
AES cryptographic protection
Flexible
No impact to user experience