Complexity With Database Encryption Methods
Most encryption implementations are protecting against the wrong threat. These methods do nothing to counter modern-day data leaks and breaches.
Common Misconceptions about How Encryption Works
Across the industry, from security professionals to auditors, there are some common misconceptions about encryption methods that a lot of people get confused about in terms of the threat model and risks that are actually being mitigated.
Without understanding the methods and what you are protecting against, it’s challenging to ensure the appropriate data protection model. Further, implementing encryption can be quite complex, with several interdependencies.
Read our article on the threat model and how common cybersecurity measures do not stop attackers in “Why you can’t stop data breaches – Part I”.
The most common at-rest encryption methods for data used today are physical disk encryption and transparent data encryption (TDE) for databases. Disk-level encryption at rest and TDE encryption was designed to protect against physical data theft or data center break-ins. But this is not how information security breaches often occur today, either in your colo or in your AWS, Microsoft, Azure, SQL Server, or Oracle cloud environments.
Attackers can easily bypass these “protection” methods because as they gain access to infrastructure or move laterally in the environment, the data can be accessed via clear text without the need for decryption keys. This fundamental gap is one of the main reasons that new malware, database server breaches, and data loss are announced almost daily and continue unchecked.
In today’s world, security teams must move more and more to a zero-trust model, which effectively assumes that networks are already compromised. In the modern-day environment, with attackers already present, security methods such as disk encryption solutions and TDE do not adequately protect your data.
The modern-day attack landscape, combined with a move to cloud infrastructure, mandates a data-centric security approach for all authorized users that protects the data values you are responsible for.
ass these “protection” methods because as they gain access to infrastructure or move laterally in the environment, the data, despite the encryption, can be accessed in clear text. This fundamental gap is one of the main reasons that new malware, data breaches and data loss are announced almost daily and continue unhindered.
In today’s world, security teams must move more and more to a zero-trust model, which effectively assumes that networks are already compromised. In the modern-day environment, with attackers already present, security methods such as disk encryption solutions and TDE do not adequately protect your data.
The modern-day attack landscape combined with a move to cloud infrastructure mandate a data-centric security approach that protects the actual data values that you are responsible for.
Below is an overview of some of the different types of data encryption algorithms & methods that are commonly available.
Disk Level Encryption
Encrypts data at the physical disk layer of a storage device and protects against physical theft of a hard drive or laptop. Operating system access provides full access to the data in the clear.
Transparent Data Encryption (TDE)
Provides the process of encrypting a database as a container on the file system. This protects against physical data theft and against access from a non-DBA who may have access to a system where the database and database backup resides. Access to the database by any user provides full access to the data and data files in the clear.
Field Level Encryption
Encrypts and configures columns or fields of data in a structured data type environment. This protects against privileged users and DBAs with access to a database, insider threats, 3rd party developers, and attackers moving laterally (east-west) in an environment from seeing sensitive data in the clear. This set encryption method is sometimes referred to as Application-Level Encryption (ALE) and denotes an encryption state.
Record Level Encryption
Encrypts data on a per row or record basis in a structured data environment using different encryption keys for different rows. These different keys help prevent oversharing of data in co-mingled data stores or multi-tenant SaaS environments and can also be applied to segment data based on classification. This method is sometimes referred to as Record Level Encryption (RLE).
All of these data encryption methods are commonly referred to as Encryption At-Rest. Perhaps part of the issue is with the term “Encryption At-Rest” because, technically, all of these methods are at-rest encryption options. But, the risk mitigation is clearly different based on the data protection method.
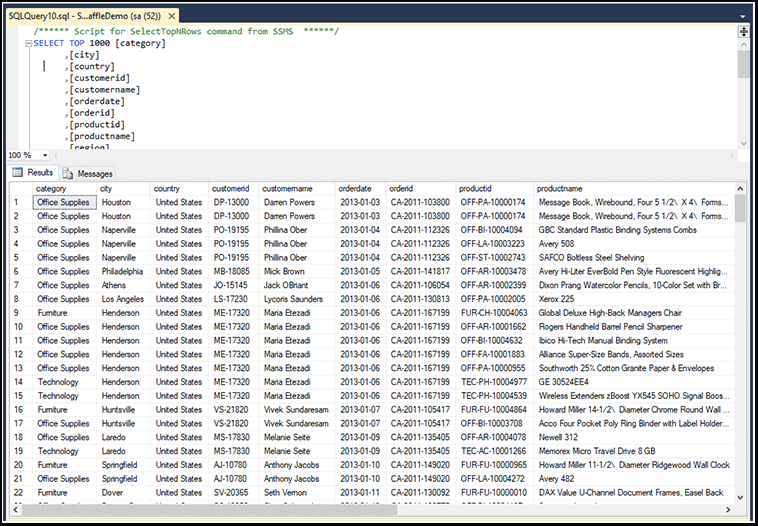
On the right is an example of Transparent Data Encryption (TDE).
As you can see, anyone with access to the database sees the data in the clear.
- It does nothing to protect against a modern-day hack or breach (most recent breaches enabled TDE uses, and data was still stolen).
- Data in the logs are in the clear, which violates compliance regulations such as PCI
- Data in memory is in the clear
- Attackers moving laterally in the network gain authentication (SSL/TLS) to access data in the clear
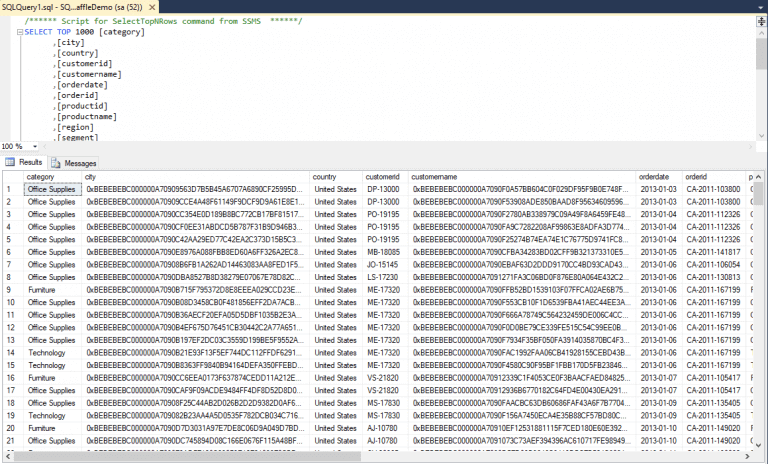
To the left is an example of Application-Level Encryption or Field Level Encryption.
- Privileged users and insiders with access to the system see the data encrypted
- Attackers accessing the system laterally through the network see encrypted data
- Data in logs are encrypted
- Data in memory are encrypted
Our Solution
Baffle delivers an enterprise-level transparent data security platform that secures databases via a "no code" model at the field or file level. The solution supports tokenization, format-preserving encryption (FPE), database and file AES-256 encryption, and role-based access control. As a transparent solution, cloud-native services are easily supported with almost no performance or functionality impact.
Easy
No application code modification required
Fast
Deploy in hours
not weeks
Powerful
No impact to user
experience
Flexible
Bring your own key
Secure
AES cryptographic
protection
Schedule a live demo with one of our solutions experts to get answers to your questions