The Future of Database Encryption
June 16, 2017
A few years ago, Baffle co-founder and CEO Ameesh Divatia penned an article called The Future of Database Encryption. This article appeared, with others like it, in the 2017 edition of the Cybersecurity Sourcebook. In this post, we have updated the information and added a link to the most recent version of the Cybersecurity Sourcebook.
For encryption to be more broadly deployed, it must become easier to consume (use) and interfere less with how applications process data.
CIOs and CISOs are starting to recognize that data security, specifically encrypting the data “in use” in databases, is critical . They scramble to adopt it before their organizations fail the next compliance audit, become victims of unauthorized access, or, worse, the subsequent major data breach. But there are several cybersecurity hurdles to clear before database encryption is more broadly deployed. Simply put, encryption must become easier to consume/use and interfere less with how applications and databases process data. Enterprise databases have the crown jewels— data that is the lifeblood of business and must be protected. This puts the spotlight on database management and relational database encryption, a necessary evil that protected enterprise assets when storage disks were stolen.
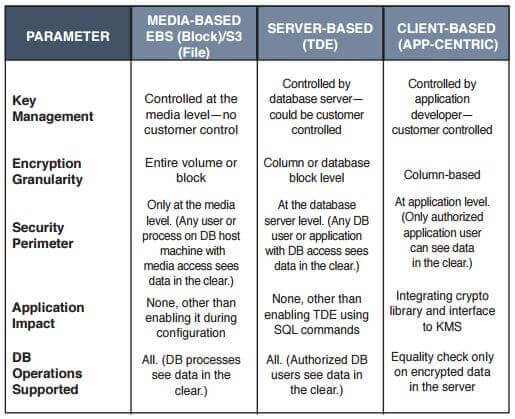
Today, encryption for sensitive data in databases is available in multiple flavors. First, there is media-based encryption, where either blocks or files are kept in an encrypted format in storage . The infrastructure/cloud service provider controls the encryption and decryption keys and the encryption/decryption process. Second, server-based or transparent data encryption (TDE) is transparent because the applications do not change, encryption is performed in the database server, and the administrator controls both the public keys as well as the private keys. In both encryption methods, the data is exposed when the database uses/processes the data, giving a DBA or any other authorized user with access to the database tables the ability to extract sensitive data with the right tools.
To counter this threat, smart application developers use application-layer encryption, where the application performs encryption within its program logic. This usually requires application developers to learn cryptography and key management systems best practices, identify the right place in the application architecture to perform encryption and make the proper function calls to encrypt and decrypt sensitive data as it is stored in the database. After encryption, the only operation possible on encrypted data is an equality check, meaning that nearly all operations previously performed by the application on the data would have to be done after the data is extracted from the database and decrypted in the application. The adjacent table describes each of the approaches and their features. This approach to encrypt data works, but getting application developers to learn and use cryptography is difficult and time-consuming, so, too often, this approach fails.
The era of “cloud first” development offers promising opportunities . We are moving to a paradigm of services being programmatically integrated into applications . To follow that model, encryption will be provided as a service to be integrated into existing enterprise workflows without any application changes and a minimum impact on DevOps practices. This includes centralized orchestration that automates encryption deployment and management and seamless key management that reliably generates, uses, stores, rotates, and retires keys to encrypt data.
Finally, the service will be delivered on a consumption basis, eliminating the need for hardware-based approaches with a barrier to entry that restricts encryption to the very high end of the market. In addition, the service would be monitored extensively, along with the ability to collect audit information that can be used to satisfy compliance requirements stipulated by governments, trade organizations, and privacy groups, such as PCI, GDPR, CCPA, HIPAA, and others.
Data encryption is the foundation of an enterprise data protection strategy. However, for enterprises to reach the critical goal of encrypting and decrypting all their sensitive data, they need a new deployment paradigm that makes the process easy to use, provides comprehensive key management, and delivers an authentic end-to-end monitoring experience.
To read more, please refer to the most recent Cybersecurity Source Book found here.