A Security Analysis Of Tokenization Systems
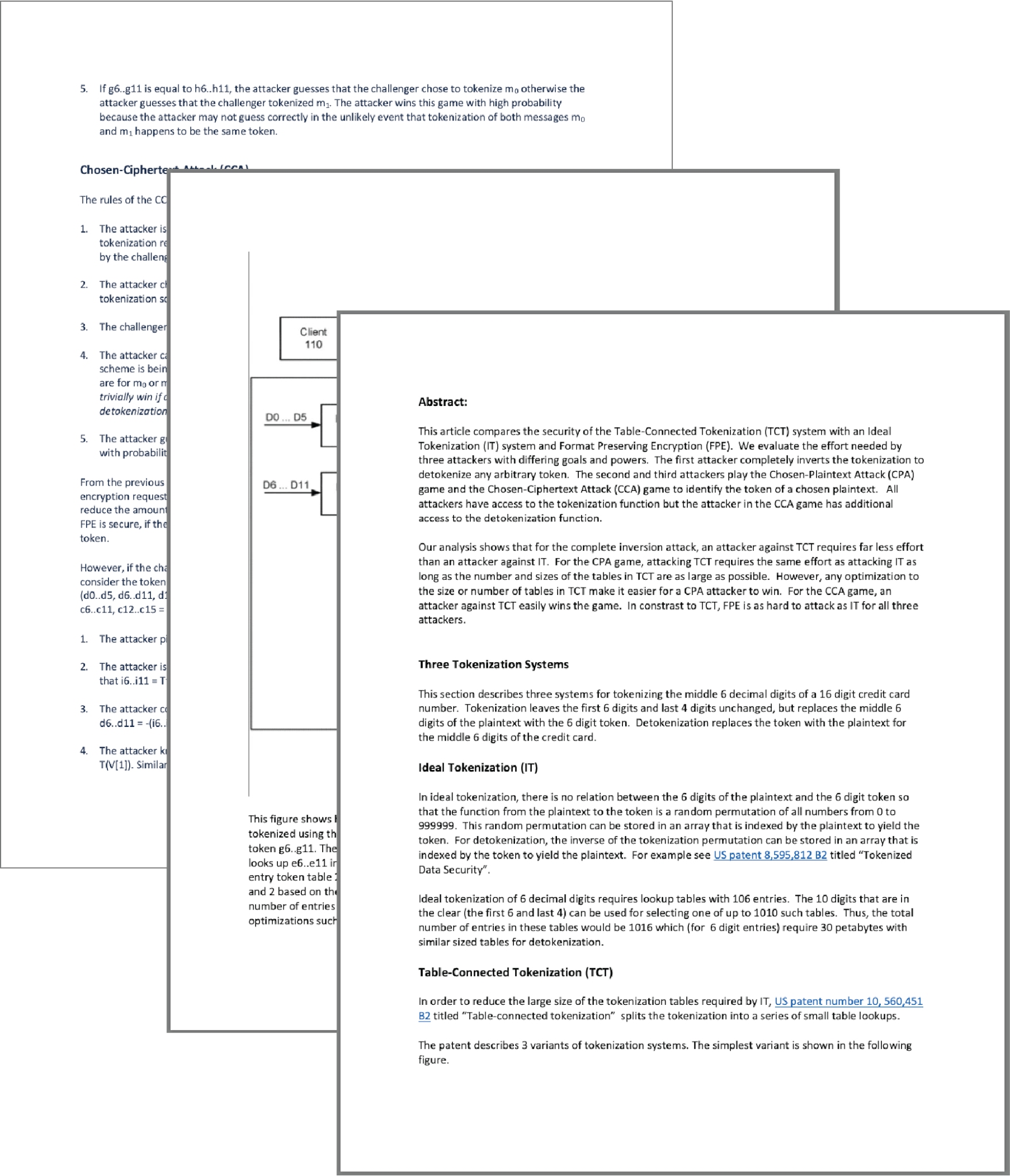
This white paper looks at specific tokenization methods and addresses how an adversary could execute attacks to gain knowledge of the transform method and ultimately reverse tokens to steal the protected data.
The analysis includes an overview of three different tokenization systems and reviews methods in-depth on how an attacker could stage cryptographic game scenarios to attack the systems.
Read the blog from our CTO, PD Kolte, here.