As privacy continues to rise in importance as a critical mandate for how businesses operate, cryptographic techniques such as homomorphic encryption and secure multi-party compute (SMPC) have received a lot more recognition. While there are similarities in terms of some of the capabilities that the two methods offer, one unique distinction that SMPC provides is the ability to restrict viewing of private data by unauthorized parties while still allowing for joint secure computation to occur on the encrypted values. This method is at the heart of Privacy Preserving Analytics and it can help enable key data analytics use cases without violating privacy.
One specific application of this technique can be applied to threat intelligence sharing and we’re seeing increased adoption across several industries, particularly financial services and health care. The operational value of threat intel sharing has long been known amongst security teams. When a peer organization has gone through the diligence of confirming threat intelligence (indicators of compromise or IOCs), it can save other security teams an immense amount of time if they have high confidence in the results of the organization that first performed the analysis. With the shortfall in security staffing projected to continue for the next several years, accelerators such as this type of collaborative confirmation can provide significant value across multiple organizations.
SMPC and Threat Intelligence Sharing White Paper
However, establishing confidence across organizations has been an Achilles heel for the security industry due to the lack of security and concerns over unintentionally exposing attribution and context about a given organization participating in an information sharing group. These areas of concerns are precisely what SMPC can help address when used for threat intel sharing.
Below is a high level architecture of one example of how secure threat intel sharing could be implemented.
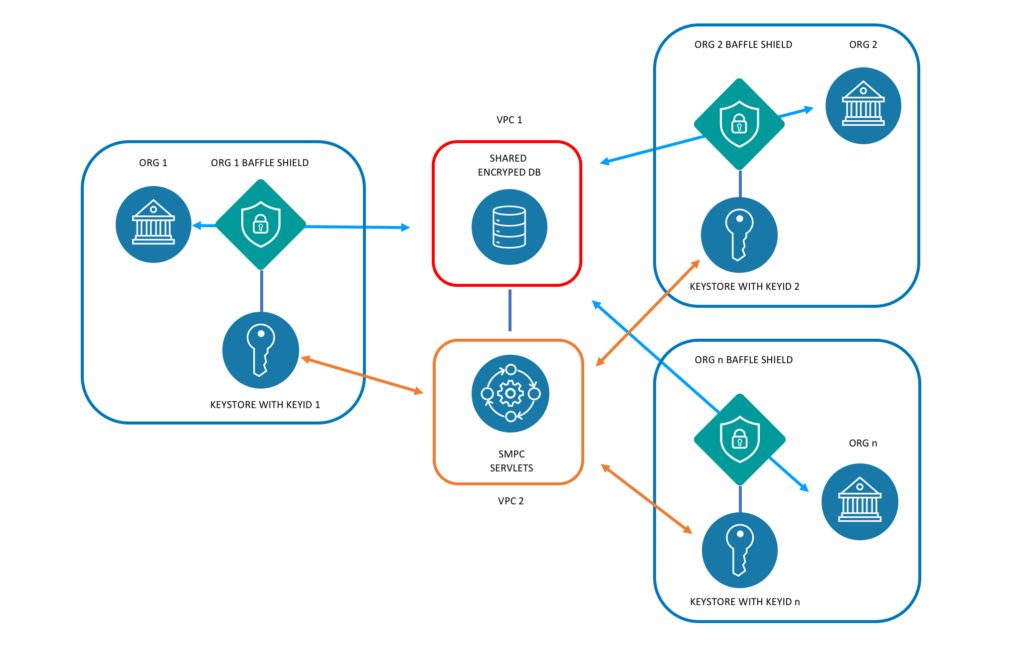
In this model, organizations 1, 2 and n are depicted each using their own encryption keys sourced from their own key store to encrypt their respective threat intelligence data. The data store is treated as untrusted entity, meaning that it is expected to operate in a hostile environment under active attack. The SMPC approach does not allow any encryption keys to live on the data tier, so effectively, no attacker can decrypt the data.
With the above implementation, no other party can view another’s data as there is no key present, but their own data remains visible to themselves. This is a multikey implementation with each organization entitled to only their own data.
While viewing another party’s data remains restricted, the ability to run aggregate lookups across organizations to confirm an IOC or view permitted context information is enabled with the above implementation. This is what facilitates secure threat intelligence sharing across multiple disparate organizations. The technical detail of how the sharing occurs is outlined further in this white paper.
Further, the same principle of securely sharing data for aggregate analytics can be applied across multiple industries and use cases. Baffle is, in fact, hosting a secure data sharing platform using the above method for organizations to use for a variety of scenarios. If you’re interested in learning more, please contact us at [email protected] or request access here.
Anonymized Threat Intel Sharing
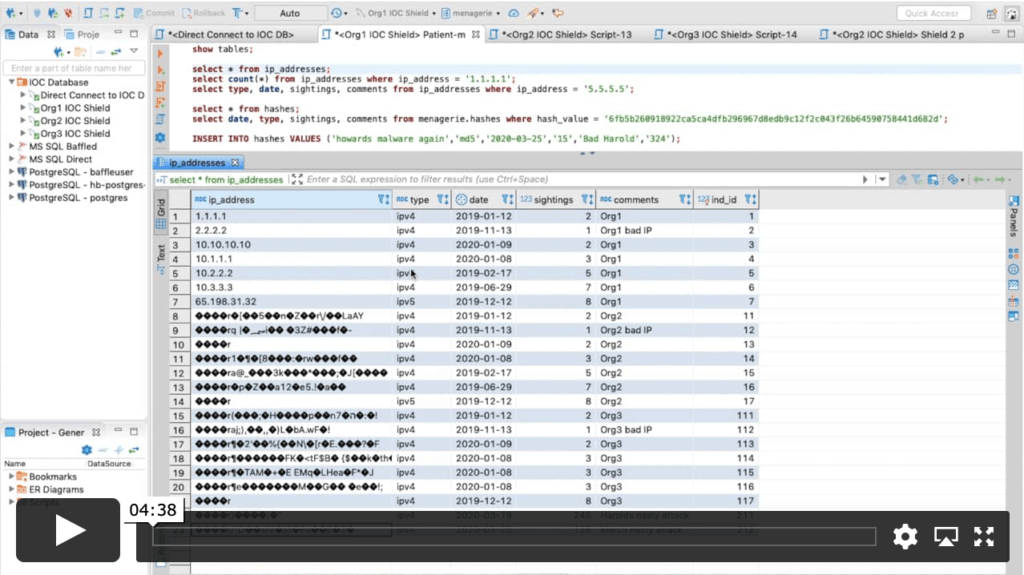
This video shows a demonstration of how multiple parties can anonymously share information with each other for purposes such as threat intelligence sharing.
Join our newsletter
Schedule a Demo with the Baffle team
Meet with Baffle team to ask questions and find out how Baffle can protect your sensitive data.
Easy
No application code modification required
Fast
Deploy in hours not weeks
Comprehensive
One solution for masking, tokenization, and encryption
Secure
AES cryptographic protection
Flexible
No impact to user experience