Over the past decade plus, we’ve seen a continued onslaught of data breaches via cyber-attacks, phishing scams, malware, ransomware, and other new cybercriminal activity. And there are no signs of it slowing down. And as we talk with prospects about cybersecurity and protecting sensitive information, we continue to get the same questions over and over again.
– How are you different than database encryption?
– How are you different from TDE (Transparent Database Encryption)?
– How are you different from data-at-rest-encryption?
The fact that this question gets asked repeatedly suggests a fundamental misunderstanding of the modern-day threat model and how specific data security controls are actually mitigating data breach risks or failing to do so.
Consider the most significant data breaches we have seen recently with Verizon, Adobe, Target, Equifax, and Yahoo, to name just a few. Unauthorized access was gained to customer data, credit card numbers, and PII (Personally Identifiable Information).
In a massive data breach, Under Armour’s MyFitnessPal was hit in February 2018, exposing over 150 million customer records, unique email addresses, IP addresses, and login credentials such as usernames and passwords. Data breach investigations found that the compromised data began to be offered for sale on the dark web the following year.
Even the healthcare giant, Anthem, wasn’t immune to a security incident that affected nearly 80 million people. Anthem was targeted by hackers who exposed Social Security Numbers, dates of birth, phone numbers, and other personal data.
As an industry, data security experts and compliance professionals have been remiss in specifying data encryption types and methods. Instead, opted for checkbox requirements, such as “sensitive data must be encrypted”. Even the much-respected CISSP certification spends more time on encryption algorithms for VPNs and handshaking vs. threat model analysis for security applied to actual data values.
The reality is that encryption methods matter, and most security professionals rely on a legacy method (encryption at-rest or TDE) that does ABSOLUTELY NOTHING to protect against modern-day attacks. (You may also be interested in our CTO’s article on how to break data tokenization here.)
Encryption at-rest and TDE were designed to protect against physical data theft or data center break-ins. This is not how data is being stolen today. We jokingly refer to this as the “Tom Cruise” threat model — a scenario where Tom Cruise (yes, the actor) breaks into a data center and drops down from the ceiling and steals your laptops and hard drives. This isn’t what’s occurring in your colo today. And it’s certainly not happeningin AWS, Azure, or GCP.
This fundamental mismatch of a security control vs. the threat is one of the main reasons data breaches continue to occur.
Simplifying Application Level Encryption White Paper
This simplified diagram below helps explain some of the gaps in the above security approaches.
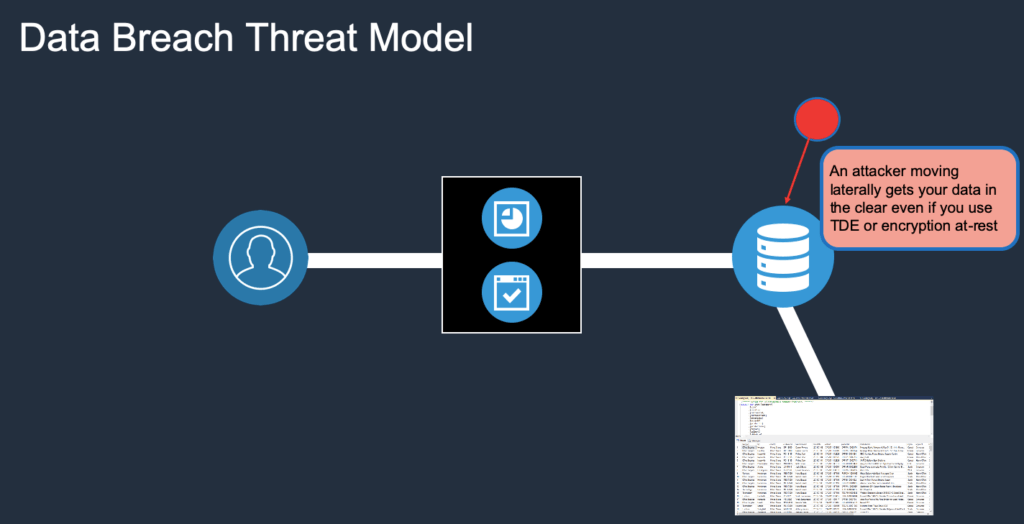
As you can see, anyone inside the network or moving laterally or with privileged access can gain access and exposes data in the clear. The encryption at-rest and TDE encryption methods are container-based encryption methods that will do nothing to stop this access. In other words, once you have access and you’rein the network, you’re in.
If your organization operates under an assumed breach posture or zero trust model, then the only logical approach, given the above scenario, is to protect your data using data-centric protections as a last line of defense.
Fortunately, we’ve seen the above questions diminish in frequency over the past couple of years as more and more customers realize that data-centric protection methods can help mitigate the risk of breaches and data theft. And we’ve continued to focus on simplifying data-centric encryption and access control methods to enable a data protection service layer for our customers who recognize that, in today’s world, “encryption” isn’tenough.
Some Useful Links:
– Encryption Complexity
– How to Simplify Encryption
– Baffle Supported Encryption Modes
– Why Data Tokenization is Insecure
– Baffle Product Overview
Join our newsletter
Schedule a Demo with the Baffle team
Meet with Baffle team to ask questions and find out how Baffle can protect your sensitive data.
Easy
No application code modification required
Fast
Deploy in hours not weeks
Comprehensive
One solution for masking, tokenization, and encryption
Secure
AES cryptographic protection
Flexible
No impact to user experience