Security for an earlier time
One of the biggest challenges with security is understanding the threats and how to properly defend against them. Just because the data is encrypted “at-rest” and you can make the auditor go away, doesn’t mean the data is protected against the real threats of the organization.
Transparent Data Encryption
Several modern databases offer Transparent Data Encryption (TDE). The database software does the encryption “transparently” at the file level when saving the data to disk. But anybody with access to the database can still retrieve the data and view it in clear text. Another method, full disk encryption (FDE) is the same idea, but instead of the database software doing the encryption, it is the underlying operating system. While the entity doing the encryption is different these methods are essentially identical.
It should be noted that the open-source version of Postgres doesn’t offer TDE. There was talk of adding it to version 16, coming late 2023, but it has since dropped off the list. Commercial versions of Postgres offer TDE, but then there is the concern of vendor lock-in. Cloud providers, such as AWS, offer FDE with their managed versions of Postgres.
The problem with either TDE or FDE is the idea was conceived when security revolved around physical security and the threat of somebody stealing hard drives. In modern data centers and public clouds, this is hardly the attack vector that keeps CISO’s up at night. From amateur hacker to state-sponsored professional, the attacker will not be physically sneaking into the data center; they will be attacking remotely. If the attacker can access the database, they can load the data, and TDE/FDE are useless.
Beyond remote attacks, the security principle of least privilege means even the DBA should not be able to access the data unless necessary to do their job. For example, the DBA shouldn’t know the company financials before the CFO or have unfettered access to employee salary and SSNs, or customer PII, PCI, and PHI data. Limits on access to the data enables the outsourcing of the database administration completely as the outsourced DBA won’t be able to access sensitive data.
Cloud providers have a “shared security model” where they keep the data centers physically safe and keep the software patches updated, but their employees may still have access (even if tightly controlled). Certainly cloud providers go to great lengths to define who can access the infrastructure/databases and under what circumstances. But in the end, their customers are responsible for setting those controls and thus it is up to those customers to keep the data safe. Full encryption outside of the database is a potent additional control that the customer should implement.
As evidence, the major credit card networks won’t let anybody accept credit cards unless they comply with PCI DSS (Payment Card Industry Data Security Standard). PCI DSS requires that credit card numbers (CCN) be encrypted at-rest, in-transit, and be properly masked in use. As an example of masking in use, the system may show only the last four digits to authorized personnel (e.g. call center personnel).
When talking about encryption at-rest, they specifically call-out TDE/FDE (in 3.5.1.2 and 3.5.1.3) and require that additional controls be added to ensure that the data can’t be accessed by remote attackers or unauthorized internal personnel.
A Modern Approach to Data Security
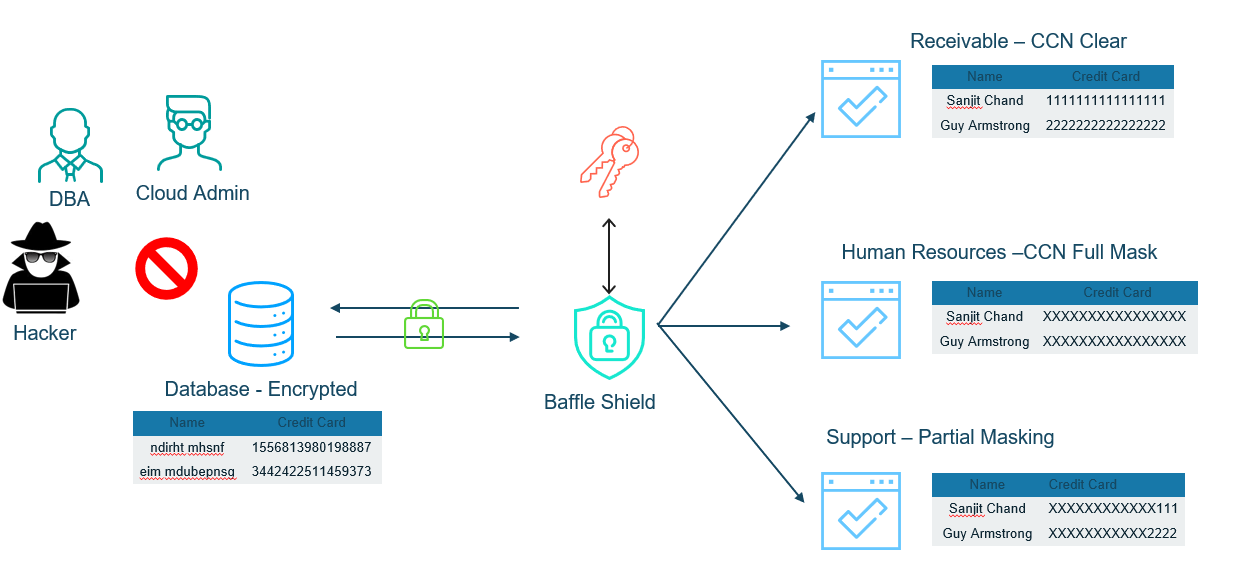
With Baffle, the data is encrypted outside of the database and then stored in a secure form in the database. This protects the data, even when someone has direct access to the database. Applications are connected through Baffle Shield that, in-turn, provides the data as required by the least-privileged role that enables them to do their job. Baffle Shield operates directly on the SQL queries and manages the key mapping which enables a no-code, fast and easy implementation.
Conclusion
TDE/FDE make perfect sense with any kind of removable storage media or a concern about the security of hard drives. These could be lost or stolen if someone gets physical access to the infrastructure.
However, for physically protected data centers and especially for public cloud, TDE/FDE are security technologies that don’t add a lot of value. Instead, a data-centric approach is required that ensures that only people with proper authorization, based on the principle of least privilege, can access the data, either partially masked or in clear text.
Ready to learn more?
Request a demo and we’ll show you how Baffle will protect the data in your databases.
Join our newsletter
Schedule a Demo with the Baffle team
Meet with Baffle team to ask questions and find out how Baffle can protect your sensitive data.
Easy
No application code modification required
Fast
Deploy in hours not weeks
Comprehensive
One solution for masking, tokenization, and encryption
Secure
AES cryptographic protection
Flexible
No impact to user experience