Resources

Supporting PCI DSS Privacy and Security Requirements
With version 4.0 of the Payment Card Industry Data Security Standard (PCI DSS), the Payment Card Industry Security Standards Council (PCI SSC) introduced the next evolution of the PCI DSS with stricter controls for data security. Baffle is the only solution that can meet PCI DSS 4.0 requirements for PostgreSQL databases. VikingCloud, a leading QSA…

Baffle for PCI DSS V4.0 Compliance
The Payment Card Industry Data Security Standard (PCI DSS) was founded in 2006 by the credit card companies Visa, MasterCard, American Express, Discover, and JCB International. UnionPay of China joined later. The purpose of PCI DSS is to create a security framework around the usage and handling of payment card and related data. This whitepaper…

Privacy Enhanced Computation with Baffle
This whitepaper outlines how Baffle achieves Privacy Enhanced Computation (PEC) via advanced encryption technology that makes PEC simple for database applications through the use of 2 complementary components: a database SQL proxy known as a Baffle Shield and a database plugin or extension known as the Baffle PEC Extension. Key Benefits: Meet current regulatory requirements…

Baffle Data Protection for SaaS
Baffle’s no code multi-tenant data security with record-level encryption ensures SaaS customers that their data is compartmentalized and under their control. Key Benefits Cryptographically partition each customer’s data inside a multi-tenant environment Allow customers to control their own data encryption keys Easy to deploy with no perceived performance impact Increase revenue with enhanced data protection…

Saxo Bank Case Study
The Data-in-Motion team at Saxo Bank was tasked with transforming their existing systems and databases to a new architecture that could handle all current and future demands. Baffle’s data protection platform empowered a central service, providing each application and entity within the organization the ability to easily de-identify and re-identify sensitive data using Format Preserving…

AWS Redshift
Baffle Data Protection Services (DPS) for AWS Redshift protects data in the cloud via a “no code” and “low code” data security mesh. De-identify the data pipeline end-to-end “on-the-fly”, and selectively re-identify data without any application changes. Conduct operations on encrypted data such as mathematical operations and wildcard search. Enable Adaptive Access Control and Dynamic Data Masking to control…
Data Privacy Cloud
Baffle Data Privacy Cloud (DPC) enables organizations to serve their own data protection services for easy consumption by developers and applications across multiple business units. Developers can make simple API calls to apply encryption for data protection and privacy. The solution runs as AWS Lambda services in your own cloud instances, allowing for dynamic scale…
Data Protection Services Data Sheet
Baffle delivers application level encryption via a “no code” model that integrates seamlessly with applications to simplify the deployment of encryption. Without modifying applications, Baffle can support search, sort and mathematical operations as well as automated workflows and machine-to-machine processing on AES encrypted data via its patented technology.
Data Protection for Snowflake
Baffle® Data Protection Service for Snowflake protects data at the field-level in data clouds. As data is ingested from on-premise databases to object stores like AWS S3 on to data clouds like Snowflake, Baffle protects sensitive data. Consumption of that data continues without any disruption including reporting and operations while the data owner holds/brings their…

A Technical Overview of Baffle Hold Your Own Key (HYOK) and Record Level Encryption (RLE)
For organizations looking to address data privacy and security concerns over data in a shared data environment, Baffle DPS offers an HYOK and row level encryption capability that can simplify implementation and management of customer-owned keys and crypto operations. Many companies do not want to spend the resources or acquire the domain knowledge to build…
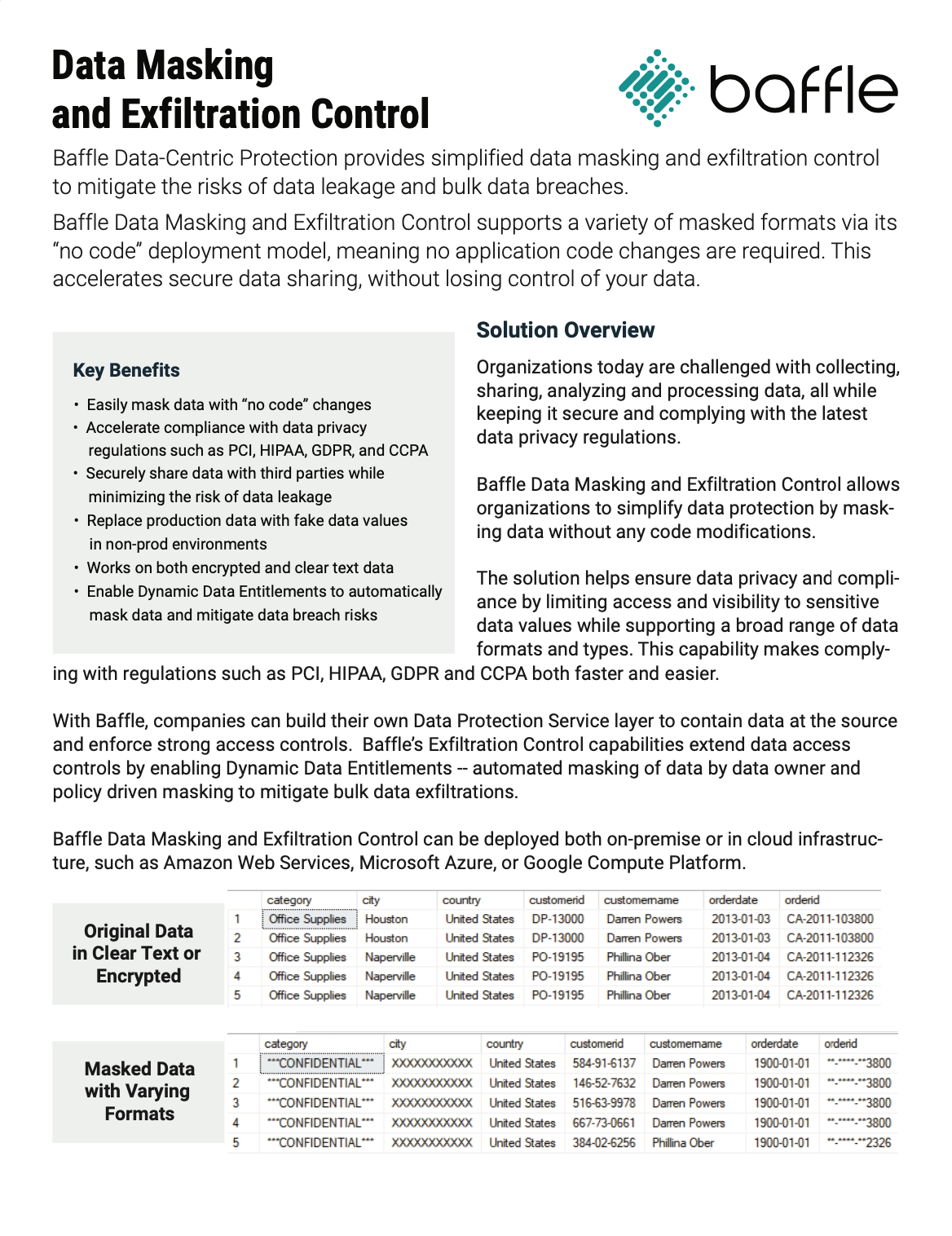
Data Masking and Exfiltration Control Data Sheet
Organizations today are challenged with collecting, sharing, analyzing and processing data, all while keeping it secure and complying with the latest data privacy regulations. Baffle Data Masking and Exfiltration Control allows organizations to simplify data protection by masking data without any code modifications.
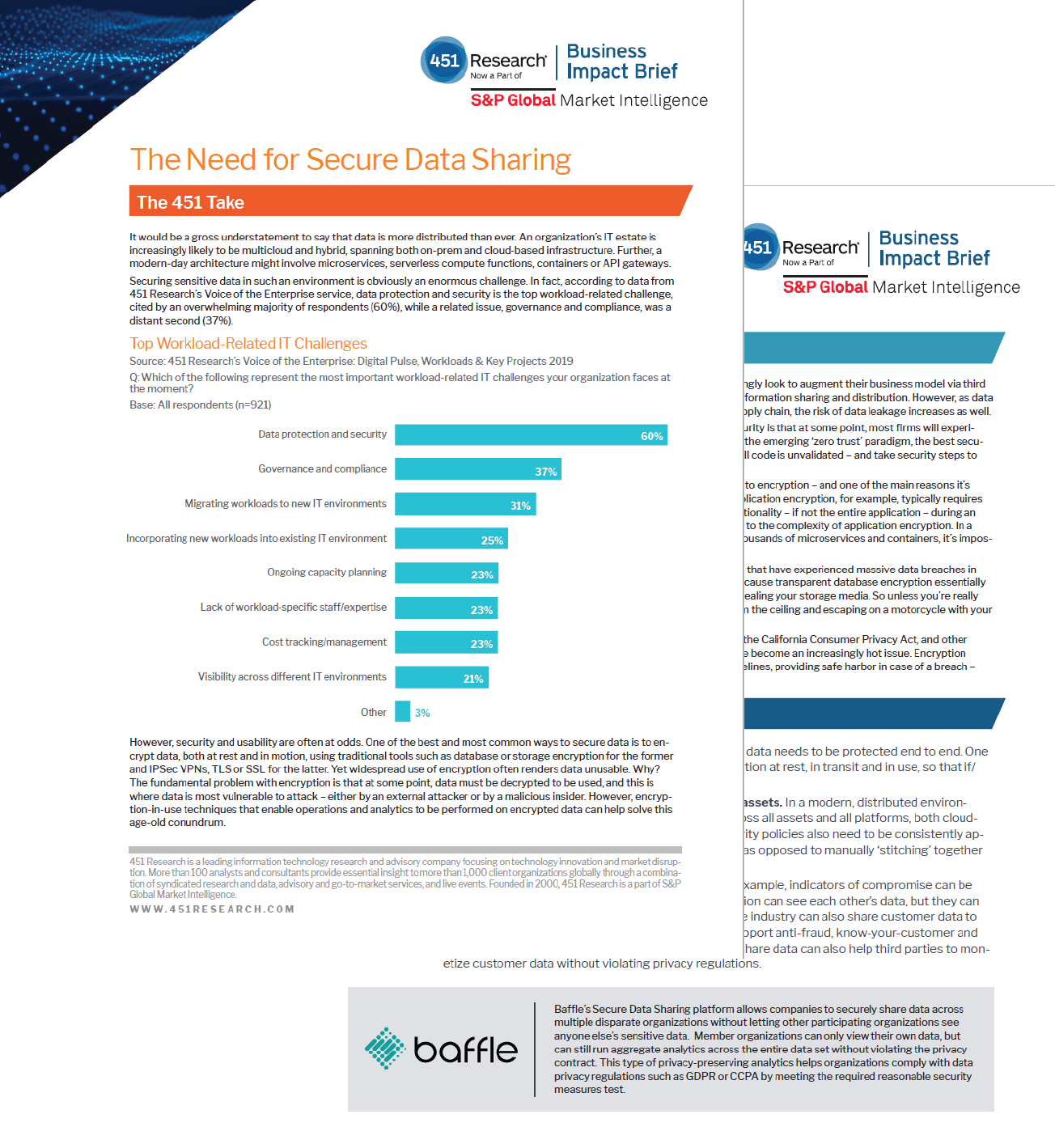
451 Research – The Need for Secure Data Sharing
It would be a gross understatement to say that data is more distributed than ever. An organization’s IT estate is increasingly likely to be multicloud and hybrid, spanning both on-prem and cloud-based infrastructure. Further, a modern-day architecture might involve microservices, serverless compute functions, containers or API gateways. Download this Business Impact Brief from 451 Research…

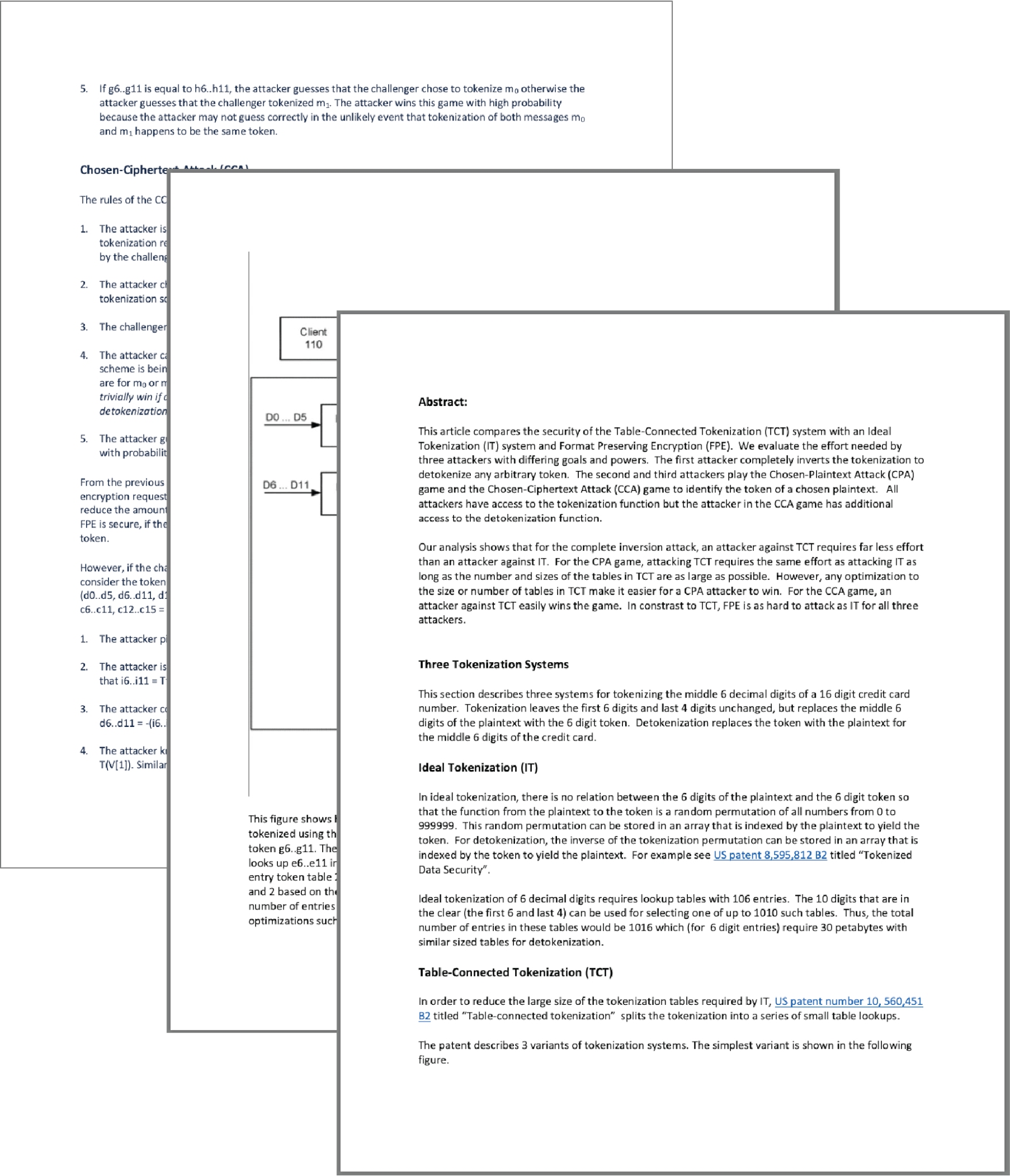
Tokenization Systems White Paper
This white paper looks at specific tokenization methods and addresses how an adversary could execute attacks to gain knowledge of the transform method and ultimately reverse tokens to steal the protected data. The analysis includes an overview of three different tokenization systems and reviews methods in-depth on how an attacker could stage cryptographic game scenarios to attack the systems.
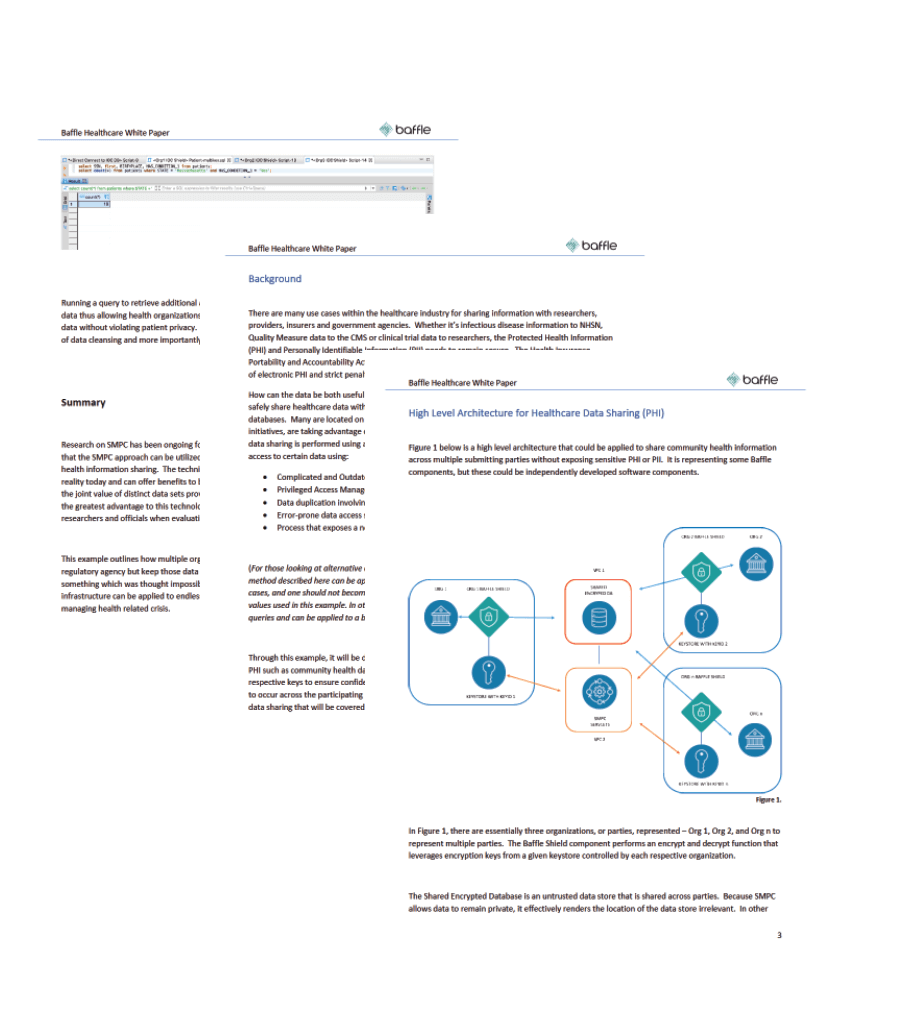
Healthcare White Paper
This white paper describes how the SMPC approach can be utilized to enable secure data sharing use cases such as community health information sharing. The technical feasibility and operationalization of such a solution is a reality today and can offer benefits to healthcare providers, payers and governing bodies operating in a distributed data environment. It describes an example of the joint value of distinct data sets providing greater value to the sharing parties.
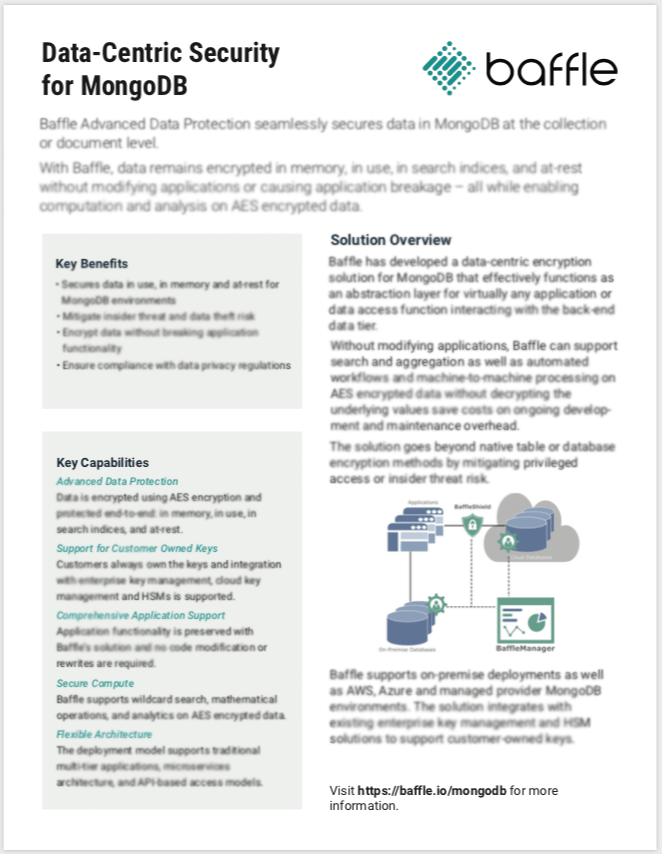
MongoDB Security Data Sheet
Without modifying applications, Baffle can support search and aggregation as well as automated workflows and machine-to-machine processing on AES encrypted data without decrypting the underlying values save costs on ongoing development and maintenance overhead.

Data Protection for Object Stores
Baffle Data Protection for Object Stores enables data-centric protection of regulated data inside unstructured files. The same field level encryption and tokenization capabilities that Baffle provides for structured data can be applied via file level encryption to unstructured and semi-structured data inside files and object storage to ensure compliance with data privacy regulations. Baffle simplifies protection of data to meet compliance as part of data pipelines.

Baffle Solution Brief
Baffle is pioneering a solution that makes data breaches irrelevant by ensuring data remains encrypted, not only when it is stored but also when it is being processed by databases and applications. With automated self-monitoring and enhanced application performance, Baffle makes it easy and feasible to provide enhanced data protection for sensitive data in public or private cloud environments. The solution includes dynamic management of customer-owned keys and the ability to protect databases at a column-level granularity.

Simplifying Encryption White Paper
Baffle's Data Protection Services aims to make encryption simple to adopt without disrupting existing application functionality – it protects data all the way up to a record level granularity and supports four modes of protection depending on the level of security desired.

Healthcare Data Sheet
HIPAA and HITECH technical safeguards specify the use of encryption safeguards for PHI, but many healthcare organizations have fallen into a false sense of security by implementing “checkbox” encryption methods that do nothing to prevent data theft.

Financial Services Data Sheet
Baffle's Data Protection Services helps secure your company’s data both on-premise and in the cloud for virtually any application via a “no code” model. Without any application changes, you can implement data-centric protection at the field or record level to mitigate the risk of data theft.

Compliance Budget Survey
Organizations continue to prioritize security and security spending, but that spending is often at odds with a more pressing business priority: regulatory compliance. This report examines how companies are prioritizing information security and compliance priorities, including which leaders control information security spending, how compliance-related priorities have shifted the overall security strategy of the organization, and…