Blog
Vulnerabilities Come in Waves
VULNERABILITY WAVE EXAMPLES In April 2014, a two year old zero day vulnerability was discovered in OpenSSL. Heartbleed represented a new finding in TLS implementations…
Overcoming the Push and Pull Between Business and Security
This morning, an article I wrote for Dark Reading called “Is Security Accelerating Your Business?” was published. Here is the link to the full article….
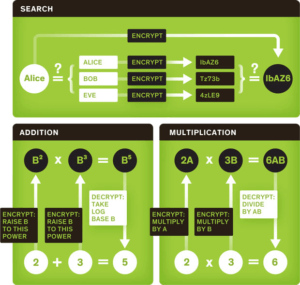
Securing data against Meltdown and Spectre with Multi-Party Compute (MPC)
The New Year has brought to light a significant vulnerability in processor architectures. In the desire to improve performance, memory isolation, which is one of…
Here comes GDPR, are you ready?
Today is May 25, 2017 – we are exactly one year away from the implementation of the most stringent privacy regulation ever enacted – the…
Why Is Homomorphic Encryption Not Ready For Primetime?
First a short lesson in history: In 1978, just a year after the RSA public-key scheme was developed, Rivest et al. published “On Data Banks…