Blog
Equifax and the Pivotal Moment for Data Privacy
Around this time last year, I published an article stating, “we have all been flooded with emails from vendors or website pop-ups with privacy notice…
FaceApp and PPA
According to the Wall Street Journal, FaceApp has been downloaded more than 95 million times world-wide, with more than 20 million of those downloads occurring…
Have We Found the Holy Grail of Privacy?
Here at Baffle, we have been beating the data protection privacy drum for years. I have enjoyed writing about the latest in the encryption industry,…
ZombieLoad: The Poster Child for the Need to Encrypt Memory Contents
The new Intel chip flaw, ZombieLoad, harkens back to the Meltdown and Spectre attacks, where we saw that security features implemented in processors are just…
Homomorphic Encryption and Multiparty Computation
Homomorphic encryption continues to entice cryptographers and academics. But is this technology ready for widespread deployment in enterprise environments? Our CEO and Co-founder Ameesh Divatia…
The Advantages and Disadvantages of Homomorphic Encryption
Note: There is an updated version of this blog post here: Advantages and Disadvantages of Homomorphic Encryption 2023 Homomorphic encryption continues to entice cryptographers and…
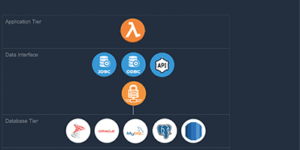
Supporting serverless — a path from legacy architecture to cloud native
Last week was quite the week for us as we announced our support for AWS Lambda serverless functions. Not only does this capability represent a…
Baffle’s Data Protection Patent Issued
Today is an exciting day for Baffle, as our first patent, “Systems and Processes for Executing Private Programs on Untrusted Computers” (U.S. 10,110,566) was officially…
The Role Encryption Plays in Protecting Healthcare Data, Driving Innovation
As the healthcare industry continues to go digital to meet patient demand and data-driven regulations, it has been heavily targeted by hackers, as patient records…
The Holy Grail of Encryption
Today, Baffle reached another milestone by delivering first-to-market capabilities enabling wildcard search on AES encrypted data without requiring any modification to an application. Achieving this…